What is Remote Access?
Remote access is the linchpin in today’s globally connected, digital-centric world. It’s not just a technological innovation but an operational necessity, a conduit that fosters seamless connectivity, amplifies operational efficiency, and transcends geographical boundaries. Below, we dissect the intricate world of remote access, unraveling its essence, applications, and intrinsic role in shaping the contemporary digital landscape.
Definition and Essence
Remote access is the technology that allows users to access a computer or a network from a distant location. The bridge dissolves physical barriers, enabling users to access files, applications, and resources as if they were physically present at the primary system or network site. Its freedom is encapsulated, empowering users with unrestricted access amidst geographical constraints.
Applications and Scope
In the multifaceted business and individual needs world, remote access finds its applications diverse and expansive. For companies, it fosters real-time collaboration, ensures continuity in the face of disruptions, and empowers a global workforce. For individuals, it’s the enabler of flexibility, allowing access to personal or work files from the comfort of home or the mobility of transit.

Business Continuity
Remote access ensures operational continuity in the unpredictable business landscape of natural disasters, pandemics, and unforeseen disruptions. Businesses can continue their operations unhampered, with employees accessing critical applications and data remotely, ensuring that productivity and efficiency remain unhindered.
Global Collaboration
In the global village, where teams are dispersed across continents, remote access fosters real-time collaboration. Distances dissipate; although geographically apart, teams are operationally integrated, working together, accessing shared resources, and driving innovations.
Individual Empowerment
For individuals, remote access is freedom personified whether accessing personal files while on vacation or tapping into work applications while at home, remote access ensures that your digital world remains at your fingertips, anytime, anywhere.
Security and Privacy
In the euphoria of accessibility, security, and privacy are paramount. Remote access, although enabling flexibility, is intricate in its security protocols. Every access is safeguarded, and every data transmission is encrypted, ensuring privacy and integrity are upheld.
Encryption Protocols
Amidst the virtual connections, encryption protocols stand as sentinels. Every transmitted data is encrypted, ensuring it’s unreadable to unauthorized entities, safeguarding data integrity and user privacy.
Authentication Mechanisms
Access is exclusive. Multiple layers of authentication mechanisms ensure that only authorized users gain access. It’s a blend of passwords, biometric verification, and tokens - an intricate dance of technological tools guaranteeing security.
The Future of Remote Access
As we catapult into the future, remote access remains relevant and is evolving. It’s becoming more secure, more user-friendly, and more integrated. Artificial intelligence, machine learning, and advanced encryption protocols are weaving into the fabric of remote access, making it a tool of convenience and a cornerstone of global business operations, individual flexibility, and digital security.
Secure Seamless Connectivity Anytime, Anywhere
In today’s rapidly evolving digital landscape, accessing your work and personal files on the go is integral to the dynamic needs of modern professionals and businesses. With the advent of globalization and the dissolution of geographical barriers, seamless, secure, and efficient remote connectivity is not just preferred - it is essential.
Achieving Operational Efficiency
The cornerstone of our remote access solutions lies in amplifying operational efficiency. Every feature is meticulously crafted to empower users with swift, uninterrupted access to their essential data and applications. In an era where agility and adaptability are paramount, we ensure that geographical constraints and time zones are no longer obstacles.
We understand that every second counts. Thus, our solutions are imbued with features that ensure instant connectivity. Whether you are a freelancer needing access to client files, a corporation with a global workforce, or someone who cherishes the flexibility of working from various locales, our remote access solutions transform these scenarios into a seamless reality.
Customized Solutions for Diverse Needs
Every individual, every business, is unique, each with a set of distinct requirements and challenges. We’ve crafted our solutions to be as versatile as they are powerful. With customization at their core, they adapt to varied operational scales and complexities. They are tailored to fit the industry standards and are personalized to your specific functional dynamics and requirements.
Safety and Security First
In the labyrinth of the digital realm, security is a sanctuary for every user. Amid escalating cyber threats and intricate malware, ensuring the sanctity of your data and privacy is our foremost priority. Our remote access solutions are armored with state-of-the-art security protocols and encryption techniques to prevent unauthorized access and cyber threats.
Encryption is not a feature but a standard; every piece of data and every communication is encrypted, ensuring that confidentiality and integrity are uncompromised. Multi-factor authentication bolsters security, adding an impregnable layer of protection that validates user identity through multiple verification mechanisms.
Round the Clock Support
Beyond the sophisticated technology and advanced features, we stand as your unwavering support. Our team of experts is available round the clock, ready to assist in every step of your journey. Be it installation, troubleshooting, or simply navigating the intricate features, we ensure expert assistance is just a call away.
Real-time Collaboration
In the realm of our advanced remote access solutions, geographical distances dissipate. Teams across continents can collaborate in real-time; access shared files, execute applications, and communicate seamlessly as if housed within the same physical space. This eradication of physical boundaries amplifies productivity, fosters innovation, and engenders an interconnected, integrated, and empowered global workforce.
Future-Ready Technology
As we steer into the future, our remote access solutions are aligned with current technological advancements and engineered to evolve. They are future-ready, scaling and adapting to the constant technological innovations, ensuring that you are always ahead of the curve your operations unhampered by technological obsolescence.
Key Features of Our Remote Access Software
Navigating the intricate world of digital communication and access can be daunting. Our remote access software is designed to ease this journey, offering a suite of features engineered for efficiency, security, and simplicity. Below, we delve deeper into the key elements that set our software apart.
Adaptable and Versatile
Our remote access solutions morph with every user’s needs. They are meticulously crafted to ensure seamless operation across varied devices and operating systems. Our software is engineered to deliver optimal performance, be it a Windows-operated PC, a macOS-driven workstation, a Linux-based system, or mobile devices powered by iOS and Android.
Seamless Integration
Integration and adaptability are at the core of our design. Users can seamlessly switch between different operating systems and devices, ensuring that technological constraints do not hamper work and access. The software integrates with the existing ecosystem, amplifying efficiency and minimizing disruptions.
Future-Ready
As technology evolves, so do we. Our solutions are engineered to adapt to emerging technologies and innovations, ensuring that users are always equipped with cutting-edge tools that are not just current but future-ready.
Enhanced Security Protocols
In the complex digital terrain where cyber threats loom large, our enhanced security protocols stand as the fortress protecting your data and privacy.
Multi-Factor AuthenticationSecurity is multifaceted. Our multi-factor authentication is a testament to this principle, necessitating multiple verification layers before granting access. It’s not just about passwords but an intricate weave of biometrics, tokens, and other authentication mechanisms ensuring that access is exclusive and secure.
End-to-End Encryption
Every piece of data and every communication is sacred. Our end-to-end encryption ensures that data remains encrypted from initiation to termination, immune to interception and unauthorized access.
Robust Firewalls
In the intricate battle against malware and cyber threats, our robust firewalls stand as unwavering sentinels, constantly monitoring, detecting, and mitigating potential dangers, ensuring that the sanctuary of your data is unbreached.
User-Friendly Interface
In the intricate world of digital access, simplicity is the ultimate sophistication. Our user-friendly interface is crafted to transform complexity into simplicity, ensuring that users of varied expertise can easily navigate.
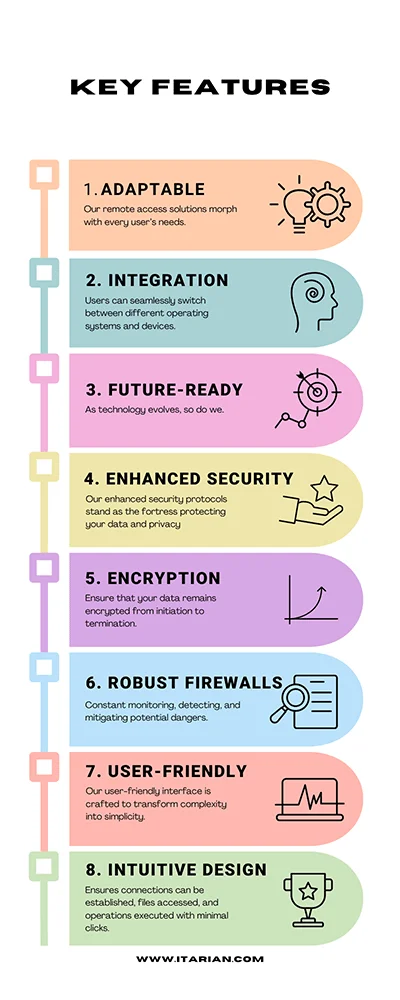
Intuitive Design
Every element and every feature is designed with the user in mind. The intuitive interface ensures connections can be established, files accessed, and operations executed with minimal clicks, maximizing efficiency and user experience.
Customized User Experience
Users are unique, and so is their journey. Our adaptable interface offers customized experiences that align with individual preferences and operational needs, ensuring that every interaction is personalized and intuitive.
Remote Access FAQ
Answer: Remote access is a technology that enables individuals and organizations to access a computer or network from a different location. This technology allows employees to access work files and applications from home or while moving, ensuring business continuity and enhancing productivity.
Answer: Yes, when implemented with robust security protocols. Remote access solutions should include end-to-end encryption, multi-factor authentication, and secure firewalls to ensure data privacy and security. Regular updates and maintenance are also essential to counter evolving cybersecurity threats.
Answer: Yes, many remote access solutions offer cross-platform support, meaning you can use various devices like PCs, tablets, or smartphones to access your work computer. However, the specific device compatibility can depend on your organization's remote access software.
Answer: The required internet speed can vary depending on the tasks you need to perform. For basic tasks, a standard broadband connection is often sufficient. However, for more data-intensive tasks like video conferencing or large file transfers, a faster internet connection is beneficial to ensure efficiency and responsiveness.
Answer: It can depend on the specific solution being used. Modern remote access solutions are user-friendly and can be set up with minimal technical knowledge. Providers often offer detailed guides and customer support to assist users in setting up, ensuring a smooth and hassle-free experience.
Answer: Employing robust security practices is essential. Utilize solutions with solid encryption, ensure that all software and systems are regularly updated, and be vigilant about cybersecurity to protect sensitive data. Also, use strong, unique passwords and enable multi-factor authentication when possible to add an extra layer of security.